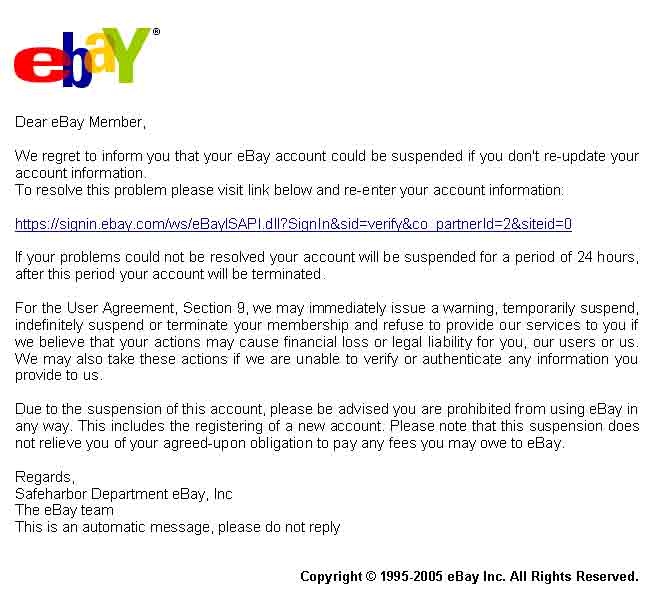
The Old Phishing Hole
Just Asking for TroubleThe "Nigerian Advance-Fee Fraud" takes in hundreds of millions of dollars each year from victims across the country; - US Secret Service
-------- Original Message -------- IMPORTANT: YOUR ONLINE ACCESS CODES MUST BE CHANGED TO ENSURE UNINTERRUPTED SERVICE. ================================================================ To enhance the level of service you receive with Wachovia Online Services, we're requiring Online Services customers to change their Customer Access Number, PIN and Codeword to a new User ID and Password. And we're enhancing the process for obtaining your Password should you ever forget it. ---------------------------------------------------------------- After you enter your current access codes, you will be guided through the following steps:
---------------------------------------------------------------- Thank you for banking at Wachovia. We look forward to serving your financial needs for many years to come. Your privacy is important to us. wachoviaemail.com/a/hBAl55iAOa3K-AQMHf2AQVtGk.AOiusd94/privacy You received this message at: ruth@chaos.net.nz © 2004 Wachovia Corporation, 301 South College Street, Suite 4000, One Wachovia Center, Charlotte, NC 28288-0013. All rights reserved. 07
When I received this message from Wachovia, I discarded it along with the 83 other phishing emails I received from 8 - 10 other banks. But then I received the following...
-------- Original Message -------- As recently noted on your Wachovia Online Services Login page, Wachovia will soon be asking you to update your login access codes. Earlier today, May 4th, you received an email from Wachovia with more information about this upcoming change. It has come to our attention that there have been concerns about the legitimacy of this email and Wachovia would like to assure you that this was a valid email sent by us. We have also posted the same message in the secure Online Services Message Center. If you would like to view this message, please login to Wachovia Online Services and go to the Online Services Home Page. From there, click the View Messages link on the left side of the screen. We apologize for any concern or questions around the earlier email message. Should you have any additional questions, please call Wachovia at 888-692-5949, 24 hours a day, seven days a week. ================================================================ You received this message at: ruth@chaos.net.nz © 2004 Wachovia Corporation, 301 South College Street, Suite 4000, One Wachovia Center, Charlotte, NC 28288-0013. All rights reserved.
So I went to the message center and found the following:
Note, however, the above message doesn't mention anything about emails that would accomplish the same thing. And why have customers do it through an email (with a screwy address) when the email could simply tell them to go online to read an important message? So I sent them a message while I was signed on and asked if they were aware that emails were being sent directing customers to go to a funny address and key in personal details - a dangerous situation. I received the following email in reply...
-------- Original Message --------
Dear Ruth Hatch, Thank you for contacting Wachovia. This message is in response to your recent communication which was received on 05/04/2004 and assigned Case ID 592221. I would like to address your concerns as to the legitimacy of the e-mail notification you referenced. Wachovia would like to assure you that this e-mail is valid and was sent by us. You may also verify this same message in the secure Online Services Message Center, by logging on to Wachovia Online Services and selecting Online Services Home from the drop down box. You may then click on the View Messages link, which is located under the heading Message Center on the left side of the screen. I hope this eases any concern you may have. Should you have any additional questions, please call Wachovia at 888-692-5949, 24 hours a day, seven days a week. Sincerely,
-------- Original Message -------- This is a reply to your reply to my recent communication - Case ID 592221. Your reply did not address my concerns. I now accept that the two emails I received came from Wachovia. My complaint is that they did not instruct me to go to wachovia.com, log in to a secure page, then change my password. Instead, they told me to click on an address that was wachoviaemail.com/a/hBAl55iAOa3K-AQMHf2AQVtGk.AOiusd94/myaccounts. This may not seem so important to you - but if you teach people that it's okay - nay, necessary - to go to an unfamiliar site and enter private password information you are setting them up to get ripped off in the future. My family are all computer-savvy. None of us could believe that Wachovia would instruct customers in behaviour as risky as that. In particular, your bank has ALREADY been a target of a scam just like this. See: bizjournals.com/charlotte/stories/2003/07/21/daily15.html Are you unable to grasp this point? Or do you just disagree that it's important? Either way, I find it distressing that a bank would do something that seems to be designed to look like a "phishing" scam - the "wachoviaemail.com" domain is, or should be, a terribly obvious giveaway. For more info on "phishing" and prevention, see: fraudwatchinternational.com/internet/phishing.shtml I'm interested in your opinion. Regards
I received the following totally unsatisfactory reply (note the new case ID) and gave up.
-------- Original Message --------
Dear Ruth Hatch, Thank you for contacting Wachovia. This message is in response to your recent communication which was received on 05/06/2004 and assigned Case ID 618895. I received your e-mail concerning the Online login information update notification. If you currently use a Customer Access Number, PIN and Codeword to access Online Services, you will be asked to update those access codes to a new User ID and Password. This change is designed to simplify login and streamline customer service for the Wachovia Online Services site, as well as increase the security of your online information and meet standards currently employed throughout the banking industry. Notification will be sent to you by letter, e-mail alerts, and login page messages in the coming weeks about the requirement to establish a User ID and Password for Online Services. Your Customer Access Number and PIN will still be required to access our telephone Voice Response Unit (VRU); however, a User ID and Password will be required to access your accounts via the web site. To obtain more information about setting up the User ID and Password, please visit our web site and access the hyperlink which is available on the Online Services Login page and listed under the Important Information notice. You will be notified as to the date you will be able to set this new login information up for access to the Online Services. I appreciate your patience during this change and apologize for any confusion this may have caused. I value your business as a Wachovia customer and look forward to continuing to serve your financial needs. If you have additional questions or concerns please contact us via e-mail or call 800-654-1276. Representatives are available to assist you 24 hours a day, seven days a week. Sincerely,
Imagine my surprise when I ran across the following the very next month - especially note the sentence I put in red bold...
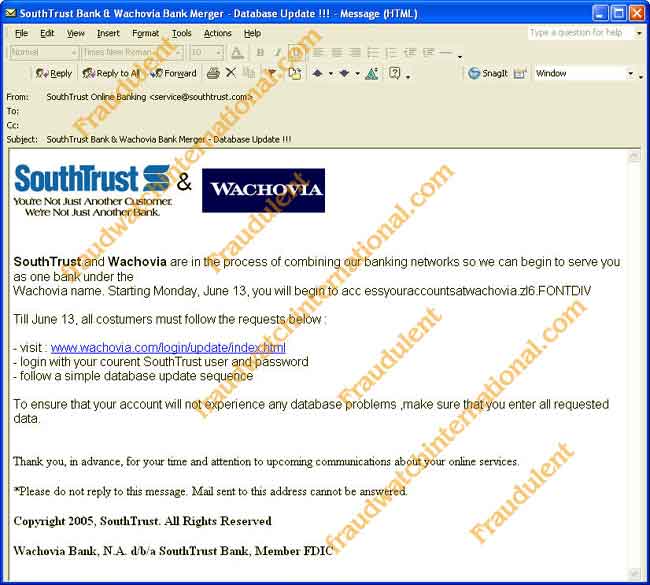
Wachovia Warns Customers on "Phishing"New York (Reuters) - Wachovia Corp. (NYSE:WB - news), the No. 4 US bank, on Friday warned customers about an increasingly common e-mail scam designed to steal personal information and money, ahead of a systems conversion next weekend affecting former SouthTrust Corp. customers. Charlotte, North Carolina-based Wachovia and SouthTrust, which it bought last November 1, are among many banks whose customers have fallen victims to "phishing" scams. Phishing lures innocent people to bogus Web sites that look like those of well-known or reputable government agencies, banks, credit card companies and retailers, and deceives them into divulging personal data. The term is derived from the act of computer thieves who "fish" for private data. "Since the beginning of the year, we have seen a rise in the number of phishing e-mails with the SouthTrust name," Wachovia spokesman Doug Caldwell said. "With our upcoming systems conversion, fraudsters are trying to take advantage of perceived vulnerabilities of customers, knowing that customers will have to change some of their log-in procedures." Caldwell said Wachovia does not know how many of its customers have been phishing victims. Wachovia said it has already notified all customers who need to update account information, and does not sent unsecured e-mails asking them to provide personal information online. It said customers should report fraudulent e-mails to abuse@wachovia.com or abuse@southtrust.com. The Anti-Phishing Working Group, which monitors Internet scams, has said up to 5% of recipients of scam e-mails respond, often suffering identity theft or financial loss. The group identified 3,930 distinct phishing attacks in April, twice as many as in the prior July. It reported an attack affecting SouthTrust as recently as May 9. SouthTrust had been based in Birmingham, Alabama. Source: www.ladlass.com 4 June 2005from Yahoo! News 3 June 2005
Source: www.fraudwatchinternational.com/internetfraud/phishing/examples/pages/southtrust_email.htm
No Trouble Telling That ALL the Following Were PhonyBecause I Don't Even Have Accounts at These Places...-------- Original Message --------
Dear Valued Customer, We have just installed our new security system which will help you to avoid frequently fraud transactions and to keep your investments in safety. Due to this technical update we are insisting our clients to verify reactivate their accounts. Please click on the link below and wait while a new window opens. Then fill out Westpac account verification form and click the 'submit' button. The verification process normally takes about 10 seconds but it may take longer during certain times of the day. When your information will be successfully updated, you will return to the main page. https://sec.westpactrust.co.nz/IOLB/newSession We appreciate your business. It's truly our pleasure to serve you. Westpac New Zealand Customer Care This email is for notification only. To contact us, please log into your account and send a Bank Mail.
-------- Original Message --------
Dear valued Customer! As part of our continuing commitment to protect your account and to reduce the instance of fraud on our website, we are undertaking a period review of our member accounts. You are requested to visit our site by following the link given below. This is required for us to continue to offer you a safe and risk free environment to send and receive money online, and maintain the Westpac New Zealand Experience. After verification you will be redirected to the Westpac New Zealand home page. Thank you. https://sec.westpactrust.co.nz/IOLB/newSession We appreciate your business. It's truly our pleasure to serve you. Westpac New Zealand Customer Care
-------- Original Message --------
Dear Bank Of The West Customer, This is your official notification from Bank Of The West that the service(s) listed below will be deactivated and deleted if not renewed immediately. Previous notifications have been sent to the Billing Contact assigned to this account. As the Primary Contact, you must renew the service(s) listed below or it will be deactivated and deleted. Renew NowSERVICE : Bank Of The West eTimeBanker with Bill Pay. Thank you, ***************************************************************************** Please do not reply to this message. For any inquiries, contact Customer Service. Document Reference: (92051208).
-------- Original Message --------
See also:
"Spear Phishing" Tests Educate People about Online Scamsby David Bank To fight computer crime, the good guys are masquerading as bad guys pretending to be good guys. In recent months, nearly 10,000 New York state employees have received email messages that appeared to be official notices asking them to click on Web links and provide passwords and other confidential information about themselves. Those who complied received gentle slaps on the wrist from William Pelgrin, New York's chief information security officer, who explained that the seemingly authentic messages were crafted by state officials "to demonstrate how realistic attackers' fake emails can seem." The exercise, along with similar ones conducted at the US Military Academy at West Point, New York, and at least two other organizations, represents a new - and controversial - approach to fending off computer hackers. By using some of the same "social engineering" techniques as the attackers, defenders hope to train users to be more careful about sharing sensitive information online. Mr Pelgrin plans to brief officials from other states about the exercise in a conference call today. "This is not a one-shot deal," Mr Pelgrin says. "I've got to reinforce that behavioural change to make it permanent." Such change is important because hackers are increasingly exploiting the weakest link in computer security - humans. Most computer users have become savvy enough to avoid obvious attempts at what security experts call "phishing" - phony email messages, often purportedly from financial institutions, that ask for personal information such as account or Social Security numbers. But many are still succumbing to a new wave of more sophisticated attacks, dubbed "spear phishing," that are targeted at specific companies and government agencies. In such exploits, attackers create email messages that are designed to look like they came from the recipient's company or organization, such as an information-technology or a human-resources department. More than 35 million of these targeted email messages to steal critical data and personal information were launched in the first half of the year, according to a report this month from International Business Machines Corporation. And use of these scams is soaring: The number of such email messages sent rose more than 1,000% from January to June, the company said. The mock phishing exercises demonstrate how effective such attacks can be. In June 2004, more than 500 cadets at West Point received an email from Colonel Robert Melville notifying them of a problem with their grade report and ordering them to click on a link to verify that the grades were correct. More than 80% of the students dutifully followed the instructions. But there is no Colonel Robert Melville at West Point. The email was crafted by Aaron Ferguson, a computer-security expert with the National Security Agency who teaches at West Point. The gullible cadets received a "gotcha" email, alerting them they could easily have downloaded spyware, "Trojans" or other malicious programs and suggesting they be more careful in the future. Mr Ferguson, who runs similar exercises each semester, said many cadets have been victimized by real online frauds. "There have been quite a few cadets who have been duped," he says. Nonetheless, he says the exercise upset some cadets, who felt it exploited their inclination to follow an order from a colonel, no questions asked. He says the new edict is, "Ask questions first, then execute." Some computer-security experts say the bogus phishing exercises can help "inoculate" users against falling for real phishing scams, much like vaccines use a broken version of a real disease to provide immunization. "This is a key defense against large-scale theft of confidential information," says Alan Paller, research director of the SANS Institute, a computer-security clearinghouse based in Bethesda, Maryland, who helped devise the New York state exercise. Still, there are potential pitfalls, including the possible loss of trust among employees for their organizations' own information-security staff. "My initial thoughts when I heard about it was 'Whoa, this sounds questionable,'" says David Jevans, chairman of the Anti-Phishing Working Group, an industry consortium. He says that although employers are within their rights to train their employees, companies should be careful before they intentionally use mock email on their customers. "You're playing with fire," he says. "Are people ever going to trust your email?" Mr Jevans, chief executive of a computer-security firm called IronKey Incorporated, argues that technical methods for authenticating email are likely to be more effective than such user education. In New York, Mr Pelgrin says he took pains to carefully design the exercise, including hiring an outside Web consultant to design the mock email pitch. "We wanted to make sure it was not too good," he says. He also enlisted AT&T Corporation to route the email messages so that they came from outside the state's own computer network, just like a real phishing attack. In the first phase, in March, nearly 10,000 employees received an email with the logo of the state's Office of Cyber Security and Critical Infrastructure Coordination. The note directed employees to a special "password checker" site. "You are required to check your password by clicking on the link below and entering your password and email address by close of business today." About 15% of the recipients tried to enter their passwords before being stopped by the automated program, which sent them a note explaining the exercise. An additional 3% tried to enter the Web address in their own browsers, a sound security practice that can deflect most attacks. In July, a second message, purportedly from the employee's own agency, asked for help fixing an Internet problem "due to a suspected cyber security event." A link took employees to a Web page that asked their email address, agency, network user name and password, and phone number. This time, only 8% of the recipients tried to interact with the fake Web site, while 5% were careful enough to enter the Web address themselves. It is too early to declare the program a complete success, but Mr Pelgrin says he plans to repeat the exercises. "Repetition is important. Vigilance is critical," he says. "The bottom line lesson was: Even if the request comes from legitimate individuals, never give out personal information." David Bank is a staff reporter of The Wall Street Journal - write to him at david.bank@wsj.com2 Source: online.wsj.com 17 August 2005
|
 Animals
Animals Animation
Animation Art of Playing Cards
Art of Playing Cards Drugs
Drugs Education
Education Environment
Environment Flying
Flying History
History Humour
Humour Immigration
Immigration Info/Tech
Info/Tech Intellectual/Entertaining
Intellectual/Entertaining Lifestyles
Lifestyles Men
Men Money/Politics/Law
Money/Politics/Law New Jersey
New Jersey Odds and Oddities
Odds and Oddities Older & Under
Older & Under Photography
Photography Prisons
Prisons Relationships
Relationships Science
Science Social/Cultural
Social/Cultural Terrorism
Terrorism Wellington
Wellington Working
Working Zero Return Investment
Zero Return Investment